- Research
- Open access
- Published:
High-capacity reversible image steganography based on pixel value ordering
EURASIP Journal on Image and Video Processing volume 2019, Article number: 54 (2019)
Abstract
In this study, an improved reversible image steganography method based on pixel value ordering (PVO) is proposed to improve the steganographic capacity. Before the steganography process, three continuous and neighboring pixels are regarded as one group for sequencing, where the maximum and minimum values are adopted for difference value calculation and the number of difference values is recorded. The pixels with more steganographic difference values in rows or columns are determined, after which the steganography and ciphertext retrieval steps are performed in the rows or columns of the digital image. The experiment results prove that the method replaces the block structure in frame selection by groups of continuously read pixels, i.e., every three pixels form a pixel group where two bits of confidential information can be hidden, thus improving the steganographic capacity effectively. Comparisons with other PVO hiding schemes confirm the superiority of the proposed scheme, which has a higher capacity and maintains an acceptable peak signal-to-noise ratio (PSNR).
1 Introduction
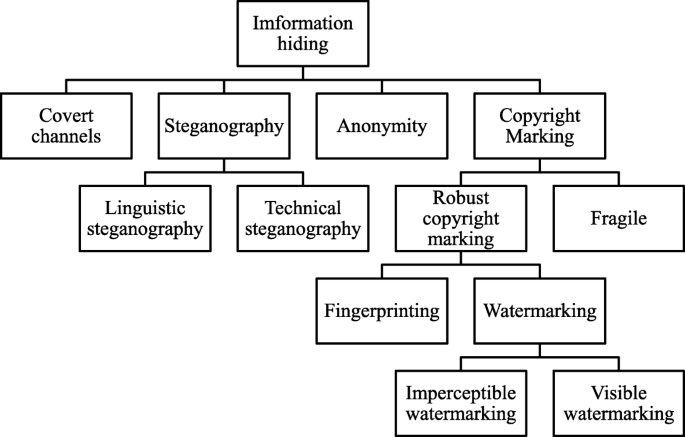
The development of information technology and the widespread use of smartphones have contributed to the ever-growing frequency of interpersonal communication in modern society. However, information can be leaked through illegal or intentional actions of personnel during information transmission, resulting in severe losses. From the perspective of historical development, information hiding is an effective way to transmit confidential information. Consequently, advanced information hiding techniques are extensively applied to various modern digital images and other media. Information hiding techniques hide confidential information and display meaningful content in such a manner that suspicion is not easily aroused. Information hiding technologies can be classified as shown in Fig. 1 [1].
Information hiding techniques are extensively utilized in various fields, such as military and commercial communications, primarily for the transmission of digital image content. Because it is difficult for the naked eye to spot the minute differences in the digital image content, human beings are usually unable to notice the hidden confidential information.
With the rapid development of information hiding technologies, methods for steganographic capacity improvement and digital image quality evaluation have emerged as a major research topic. Steganography techniques include the least-significant bit (LSB) [2], pixel-value differencing (PVD) [3], and subsequently proposed substitution and combination methods of PVD and LSB [4]. The steganography method based on LSB and PVD is classified as a lossy data hiding approach. Further, the histogram shifting method [5] is a lossless data hiding approach that causes the least distortion to images and results in higher image quality after steganography; hence, it has attracted considerable attention from researchers [6,7,8]. Zhang proposed a novel reversible data hiding scheme for encrypted images. In the proposed scheme, after encrypting the entire data of an uncompressed image by a stream cipher, the additional data is embedded into the image by modifying a small proportion of the encrypted data [9]. Qin et al. proposed a novel joint data hiding and compression scheme for digital images that uses side match vector quantization (SMVQ) and image inpainting. The data hiding and image compression functions are seamlessly integrated into one single module [10]. Huang et al. proposed multi-level reversible data hiding with a pyramidal structure. Considering the inherent characteristics of the original content and their spatial relationships, a pyramidal structure is employed in which more secret information is hidden with similar quality in the output image [11].
To further improve the steganographic capacity, prediction error histogram shifting (PEHS) steganography, which combines the prediction error (PE) and histogram shifting (HS), has emerged as a well-known technique among currently used lossless data hiding methods [12,13,14]. In the lossless data hiding approach based on pixel value ordering (PVO) [15], a digital image is sliced into several blocks that are arranged according to the pixel value in each block. Two differences are obtained through subtraction of the largest pixel value and the second largest pixel value as well as subtraction of the smallest pixel value and the second smallest pixel value. However, only the largest pixel value, the smallest pixel value, and their difference within blocks are used for steganography to achieve such excellent image quality. Therefore, there remains a room for improvement of the steganographic capacity. Toward this end, researchers have proposed improved steganography based on PVO [16,17,18,19]. The various steganographic methods are compared in Table 1. LSB, PVD, and PVD+LSB are lossy data hiding approaches (no additional information is embedded)—after the extraction of the ciphertext, the original cover image cannot be restored. HS, PEHS, and PVO are lossless data hiding approaches (additional information is embedded)—after the extraction of the ciphertext, the original cover image can be restored. The lossy data hiding approach is suitable for cases where a large amount of ciphertext needs to be transmitted, and the cover image is not required to be restored. The lossless data hiding approach is suitable for transmitting the ciphertext and then recovering the carrier image. The embedded capacity (EC) of various steganographic methods was generated by the experiment. The values in parentheses represent the ratio of embedded capacity divided by the image size (maximum possible embedding capacity). The experimental image used in this study is 512 × 512 grayscale image, and the image size is 262,144.
Steganographic methods employ various techniques to provide security. LSB hides the encrypted message by replacing the least significant bits of the pixels of the cover image. However, sequentially flipping the LSBs can result in the pair of value (PoV) problem [20], which has been explored by many steganalysis methods, such as x2 [20] and RS [21]. For steganalysis of PVD-based embedding, Zhang and Wang [22] analyzed the histogram of stego images embedded by PVD and proposed a steganalysis technique that attacks the original PVD successfully by exploiting the step effect in the PVD histogram. For steganalysis of HS-based embedding, based on a special feature when all the pixels of the peak point are used to embed the secret message, Kuo et al. [23] proposed specific steganalysis methods to detect Ni’s method. Liu and Liu [24] proposed a steganalysis method based on the payload invariant features to detect the histogram shift-based steganography in Ni’s method.
On the basis of the background and motivation presented above, in this work, an improvement was achieved mainly by focusing on PVO. The contributions of this work were listed as follows:
-
(1)
The proposed PVO scheme has a higher capacity than the other PVO methods while maintaining an acceptable PSNR, demonstrating the superiority of the proposed hiding scheme.
-
(2)
To verify the suitability of the proposed PVO scheme for various image types, 9,074,512 × 512 grayscale images were selected from the BOWS-2 image databases as raw images. Experimental results proved that the proposed PVO scheme is applicable to different types of images.
The remainder of this paper is organized as follows: Section 2 summarizes the literature related to this research. Section 3 explains the proposed method. Section 4 discusses the related experiments conducted and the proposed hiding scheme. Finally, Section 5 presents our conclusions.
2 Literature review
2.1 Original PVO
PVO is a reversible digital image steganography method proposed by Li et al. [15]. In this method, the digital image is sliced into several blocks and ordering is performed according to the pixel values in each block. The difference between the largest pixel value and the second largest pixel value and the difference between the smallest pixel value and the second smallest value are obtained for steganography with 1 or − 1 as the peak value point b. The steganography steps are shown in Fig. 2.
Steps in the PVO steganography method. (1) Cover image slicing. (2) Block pixel ordering. (3) Construction of the location map LM(i). (4) Compression of the location map. (5) Setting of the block threshold. (6) Processing of extra information. (7) Recording of extra information. (8) Hiding of confidential information. (9) Accomplishing steganography of the original cover image according to step 7 until the confidential information is completely hidden
The ciphertext retrieval steps are shown in Fig. 3.
2.2 Improved PVO
On the basis of the PVO proposed by Li et al. [15], Peng et al. [16] proposed the improved PVO (IPVO) for reversible digital image steganography. In contrast to PVO, where the differences are obtained from the subtraction of the largest and the second largest pixel values and the smallest and the second smallest pixel values inside the calculation blocks, the subtraction order is determined according to the reading order. In other words, the obtained differences can be positive or negative, and more differences are obtained compared to PVO. Further, “0” and “1” are applied as the peak points of differences for steganography. Thus, compared to PVO, IPVO achieves a better peak signal-to-noise ratio (PSNR) value under higher steganographic capacity [25].
2.3 PVO multi-pixel modification
On the basis of the PVO proposed by Li et al. [15] and the IPVO proposed by Peng et al. [16], Chen et al. [19] proposed a digital image steganography method based on pixel order exchange and multi-pixel modification, called PVO multi-pixel modification (PVOMM). Compared to PVO and IPVO, after accomplishing the ordering of block slicing, the order in PVOMM is the largest, second largest, second smallest, and smallest pixel values. The second largest pixel value acts as the benchmark for this block, and subtraction of that value from the largest, second largest, and smallest pixel values is conducted. When four pixel values constitute a group, three differences can be obtained. However, the scenario that the largest and the second largest pixel values simultaneously meet the steganography conditions must be excluded. Thus, it is feasible to restore the original cover image without influencing the original pixel ordering positions. Table 2 compares and contrasts the three PVO-based methods [25].
3 Proposed methods
3.1 Pixel group selection methods
The aim of the study was to improve the steganographic capacity by modifying the original PVO method. In addition to adjusting the block selection size, the middle pixel value in the ordering block is used. The middle pixel value is subtracted from the maximum and minimum pixel values, which yields more differences compared to PVO.
The PVO methods discussed above employ the block as the core component; hence, steganography is conducted by using different steganographic algorithms or by selecting expressions after adjusting the block size, depending on which the steganographic capacity or image quality is improved. However, such improvement is limited within the block framework. Therefore, in this study, pixel-by-pixel processing, which has not been used previously, is used to read the pixel values in order in columns or rows. Furthermore, calculations are performed by regarding every three pixel values as one group.
In this study, to maximize the steganographic capacity of a digital image, before image steganography, reading in order in rows and columns (see Fig. 4) is performed, respectively. After obtaining the available steganographic capacity of the digital image for comparison, the reading method of the digital image is recorded. In the same digital image, the reading position of the first and the last pixel values remains the same in row or column reading; hence, the reading method will be recorded in the last pixel value in the entire digital image by the LSB as the first restored information after determining the reading method.
3.2 Steganography and ciphertext retrieval methods
The following are the steganography and ciphertext retrieval methods:
Step 1: The LSB of the final pixel value in the digital image will be used to indicate whether the digital image is read in row or column order. This leads to the advantage of lossless restoration of the stego image. Thus, the final pixel value of the cover image is transformed into the binary format, and it is recorded as 0 or 1.
Step 2: The cover image is read in row and column order, and the differences are calculated. If the difference is maximum while reading in rows, it is recorded as 1. If the difference is maximum while reading in columns, it is recorded as 0. This value is stored in the final pixel value of the digital image by using the LSB.
Step 3: Block pixel ordering. The sliced area pixel values p1, p2, and p3 are rearranged in order, through which the sequences pσ(1), pσ(2), and pσ(3) are obtained, where pσ(1) ≥ pσ(2) ≥ pσ(3).
Step 4: Construction of the location map LM(i). In this method, the largest or the smallest pixel value is adjusted; hence, the overflow problem can occur if the largest or the smallest pixel value is 255 or 0, respectively. Therefore, it is necessary to determine whether the block is an overflow block before the steganography steps; the relevant equation is given below.
If the block satisfies the conditions of Eq. 1, the block is an overflow block that is marked as LM(i) = 1. If there is no overflow problem, LM(i) = 0.
Step 5: Compression of the location map. The location map LM(i) is a series of binary information of length k that is compressed into lclm through arithmetic coding. There are fewer blocks with overflow problems in the original cover images; hence, there are fewer points where LM(i) = 1. Through arithmetic coding, lossless compression can be used to compress the location map in order to reduce the production of extra information.
Step 6: Processing of extra information. The information used during the steganography process of the original cover image is listed below:
-
If the evidence is read in row or column order, 0 or 1 is recorded by the final pixel value, respectively.
-
The final index value of the extra information (kend): ⌈log2N⌉ bits, N = m × n.
-
The length of the compressed location map (lclm): ⌈log2N⌉ bits.
-
The compressed location map lclm.
-
All the extra information above uses 1 + 2⌈log2N⌉ + lclm bits in total.
Step 7: Recording of extra information. The aforementioned extra information is hidden in the original cover image by using the LSB; the replaced bit is represented by SLSB and hidden in each block along with the confidential information.
Step 8: Hiding of confidential information. In the block LM(i) = 0 without overflow problems, the largest and the smallest pixel values among the pixel values after ordering according to step 3 are selected to be subtracted along with the second largest pixel value, through which two differences, dmax and dmin, are obtained using the following equations.
Next, the differences 1 and − 1 are used for hiding the confidential information b. In view of the differences larger than 1 or smaller than − 1, 1 is added to or subtracted from the largest or the smallest pixel value for difference shifting. When the difference is 0, there is no operation. The new pixel values \( {d}_{\mathrm{max}}^{\prime } \) and \( {d}_{\mathrm{min}}^{\prime } \) are obtained after accomplishing difference shifting according to the conditions above. The steganography equations are given below.
where b ∈ {0, 1} is a data bit to be embedded. Then, the new largest and smallest pixel values are calculated according to the original largest and smallest pixel values using the following equations:
Finally, the stego image is obtained after replacing the original pixel values. The step of hiding confidential information is completed.
Step 9: Steganography of the original cover image is carried out according to step 8 until the confidential information is hidden completely. The stego image X′ after steganography is obtained.
A flowchart of the steganography method proposed in this study is shown in Fig. 5.
Flowchart of the steganography method proposed in this study. The steganography steps proposed in this study are described as follows. (1) The LSB of the final pixel value in the digital image will be used to indicate whether the digital image is read in row or column order. (2) The cover image is read in row and column order, and the differences are calculated. (3) Block pixel ordering. (4) Construction of the location map LM(i). (5) Compression of the location map. (6) Processing of extra information. (7) Recording of extra information. (8) Hiding of confidential information. (9) Steganography of the original cover image is carried out according to step 8 until the confidential information is hidden completely
The ciphertext retrieval steps of the steganography method proposed in this study are as follows:
-
Step 1: Transform the final pixel value of the stego image into the binary format; read the final value as 0 or 1.
-
Step 2: Read the values extracted from step 1 in rows or columns targeting the stego image.
-
Step 3: Read the extra information, i.e., 1 + 2⌈log2N⌉ + lclm bits.
-
Step 4: Read the pixel values in order and list them with every three pixel values as one group. Obtain the sequence of pixel values p1, p2, and p3; list them and obtain the sequence pσ(1), pσ(2), and pσ(3), where pσ(1) ≥ pσ(2) ≥ pσ(3).
-
Step 5: According to the extra information, determine whether the sequence is an overflow block.
-
Step 6: If there is no overflow problem, the selection region is restored for ciphertext retrieval and pixel value restoration using the equations given below.
where b ∈ {0, 1} is a data bit to be extracted.
-
Step 7: Restore the cover image. Ciphertext retrieval and restoration are accomplished successively according to step 4, step 5, and step 6, through which the original cover image X is obtained.
A flowchart of the ciphertext retrieval process in the steganography method proposed in this study is shown in Fig. 6.
Flowchart of ciphertext retrieval in the steganography method proposed in this study. The ciphertext retrieval steps of the steganography method proposed in this study are described in Fig. 4
4 Experimental results and discussion
Improvement in the steganographic capacity of digital image steganography based on PVO was the main focus of the preliminary construction period of this study. Thus, in this study, an adjustment was made for calculation based on consideration of every three pixel values as one group, after which the steganographic capacity of the digital image was maximized through scanning in rows and columns.
The proposed PVO hiding scheme was then experimentally evaluated to assess whether its algorithm can increase the hiding capacity while maintaining the acceptable image quality. We also compared the results of the proposed PVO scheme to those of conventional PVO hiding methods to verify its efficiency. The experimental environment, procedures, and results are presented separately below.
4.1 Experimental environment and procedure
The software and hardware experimental environments used in the experiments were as follows:
-
(1)
Hardware environment: Intel(R) Core(TM) i5-4570 CPU at 3.20 GHz 16 GB RAM notebook.
-
(2)
Simulation program: MATLAB was used to implement both the proposed and conventional PVO hiding schemes.
-
(3)
Secret message: the random number generator in MATLAB was used to simulate the ciphertext in the experiments.
-
(4)
Test images: eight 512 × 512 grayscale test images that are widely used in the information hiding field were employed in this study (as shown in Fig. 7), including images with complex and smooth textures, images with portrait and landscape orientations, and images of goods and transportation.
-
(5)
Image databases: to verify the suitability of the hiding scheme for various image types, 9074 512 × 512 grayscale images were selected from the BOWS-2 [26] image databases as raw images (some example images are shown in Fig. 8).
Sample image of BOWS-2 image databases [26]. Sample image of BOWS-2 image databases. To verify the suitability of the hiding scheme for various image types, 9,074,512 × 512 grayscale images were selected from the BOWS-2 image databases as raw images
4.2 Steganographic image quality analysis methods
In this study, the PSNR value [27] and SSIM index [28] are used as referential evidence for image quality evaluation. The PSNR expressions are given below.
As a widely used objective measure for evaluating image quality, the mean square error (MSE) indicates the mean square deviation of each pixel value in the cover image and the stego image, and it is used to calculate the PSNR value. In general, the larger the PSNR value, the lesser is the distortion. PSNR is commonly used to objectively evaluate information hiding technologies.
SSIM is used for measuring the similarity between two images. The SSIM index is a full reference metric; in other words, the measurement or prediction of image quality is based on an initial uncompressed or distortion-free image as a reference. SSIM is designed to improve traditional methods such as PSNR and MSE [29]. The SSIM expression is as follows:
where μx is the average of x; μy is the average of y; \( {\sigma}_x^2 \) is the variance of x; \( {\sigma}_y^2 \) is the variance of y; σxy is the covariance of x and y; c1 = (k1L)2and c2 = (k2L)2 are the two variables to stabilize the division with weak denominator; L is the dynamic range of the pixel values (typically this is 2#bits per pixel − 1); k1 = 0.01 and k2 = 0.03 by default [29].
4.3 Analysis of experiment results
According to the block selection explained in Section 3, the pixel values are read in order in rows or columns, and the calculations are performed with every three pixel values as one group. The calculation results are summarized in Table 3, which shows that the number of differences of pixel values can lead to different results due to reading in rows or columns, and the results will influence the steganographic capacity of the entire digital image. Further, from Table 3, it can be seen that 1, 0, and − 1 appear most frequently among the differences of each digital image. However, according to the method proposed in this study, if steganography is conducted on the parts whose differences are “1 and 0” or “0 and − 1,” the same pixel values may remain after steganography. For instance, if the information 1 is hidden in the pixel group whose difference is 0 or the information 0 is hidden in the pixel group whose difference is 1, the new difference 1 after steganography will be obtained in both scenarios, leading to incorrect ciphertext retrieval. Therefore, in this study, parts whose differences are 1 and − 1 are used for steganographic procedures.
According to the statistical results of Table 3, images with sums whose pixel values are 1 and − 1 read in rows and columns are compared (as shown in Table 4). The proposed PVO hiding scheme calculated the difference by row and column respectively and determined the direction of the data bit to be embedded by the higher sum of the differences. By judging the sum of the differences, the steganographic capacity can increase about 3.8–20.29%. Thus, the average steganographic capacity increment is 9.15%.
After ciphertext embedding in the used cover images according to the steganography steps proposed in this study, the steganographic capacity (bits), the capacity as a percentage of the image size (description in brackets), the PSNR values, and the SSIM index of PVO and PVOMM were compared. The experimental results are summarized in Table 5. Except for Mandrill, the steganographic capacity obtained by the steganographic method for each digital image is higher than that of PVO and PVOMM. The average steganographic capacity and the quality measured by the standard PSNR value of the digital images are compared to those of PVO. The steganographic capacity is improved by approximately 4600 bits while the PSNR value is reduced by approximately 1.5 dB. Compared to PVOMM, the steganographic capacity is improved by approximately 1200 bits while the PSNR value is improved by approximately 0.6 dB. It can be inferred that the method proposed in this study leads to the improvement in the steganographic capacity and digital image quality.
In Table 5, it can be seen that the steganographic capacity of Mandrill is the least. From its image characteristics, Mandrill is a digital image with a relatively complex texture and belongs to digital images with the least steganographic capacity in PVO and PVOMM. However, for the digital image F16, its steganographic capacity in PVO, PVOMM, and the method proposed in this study is maximum. It can be inferred from this result that F16 is a digital image with a smooth texture, similar tones, slight differences between neighboring pixel values, and no complex blocks or colors of different darkness degrees. More differences for steganography can be obtained in the case of similar extracted neighboring pixel values and steganography based on PVO. In other words, in digital images with smooth textures, steganography based on PVO can achieve a higher steganographic capacity and maintain a certain digital image quality compared to digital images with complex textures.
To prove that images belonging to complex or smooth textures affect the steganographic capacity of PVO, the statistical kurtosis coefficient was used to analyze the distribution of the digital image in a two-dimensional pixel block and a determination made as to whether the digital image contains a large number of identical pixels in the two-dimensional pixel block. Through threshold value judgment, the block is determined as a complex or smooth texture block. The threshold value of the kurtosis coefficient used in this study was 0.2. Blocks with a kurtosis coefficient greater than 0.2 represent smooth areas of image texture. Blocks with a kurtosis coefficient of less than 0.2 represent complex areas of image texture. In Table 5, it is clear that the steganographic capacity of Mandrill is the lowest and that of F16 is the highest. Therefore, this study divided these two images into 64-pixel blocks, respectively (as shown in Fig. 9), and calculated the kurtosis coefficient of the 64-pixel blocks. In Fig. 9 (a), it is clear that 20 groups of 64-pixel blocks of F16 had kurtosis values greater than 0.2. In Fig. 9 (b), it is clear that Mandrill’s 64 groups of pixel blocks have no kurtosis values greater than 0.2. It can be seen in Fig. 9 (a) and (b) that F16 is a smooth texture image, so its steganographic capacity is relatively high; whereas, relatively speaking, Mandrill is a complex texture image, so its steganographic capacity is low.
Rate-distortion curves of embedding bits using the proposed PVO with respect to test image quality are shown in Fig. 10. For Li’s PVO, Chen’s PVO, and the proposed PVO, we varied EC from 5000 bits to its maximum with a step size of 5000 bits. The figure shows that the capacity of the proposed method is superior to that of the state-of-the-art methods in most cases, while maintaining an acceptable PSNR, demonstrating the superiority of the proposed PVO hiding scheme.
To assess the suitability of the proposed method to databases with different patterns, a further 9,074,512 × 512-pixel grayscale images were selected from the BOWS-2 [26] image databases as raw images. The proposed hiding scheme was then used to hide data and generate stego images in these images. The first row in Table 6 shows the mean value of the hiding capacity of the proposed PVO, Li’s PVO, and Chen’s PVO for the BOWS-2 image databases. The mean value of the hiding capacity of the proposed PVO is the best. The second and third rows in Table 6 show respectively the mean values of the PSNR and SSIM index for the BOWS-2 images. The mean values of the PSNR and SSIM index of the proposed PVO are inferior to those of Li’s and Chen’s PVO. The embedding capacity is higher compared to their methods while there is only a slight decrease in the SSIM value and a more severe one in the PSNR value. The results of a performance comparison with those of the PVO hiding schemes proposed by other researchers confirm that the proposed scheme has a higher capacity than the other methods while maintaining an acceptable PSNR, demonstrating the superiority of the proposed hiding scheme.
4.4 Security analysis against second-order SPAM features
Penvy et al. [30] presented second-order SPAM features for the detection of steganographic methods that embed in the spatial domain. To prove the security of the proposed method against the second-order SPAM features, 9074 cover images were retrieved from the BOWS-2 image database and the corresponding stego images of the proposed method were used to carry out the following experiment. The training image sets consisted of 4537 cover images and 4537 stego images for the proposed steganography algorithm. The remaining cover images and stego images were used for test image sets. The first step was to extract the 686 features of SPAM of training images. Furthermore, the stego images and cover images were given diverse labels. The purpose of the different labels used in the PNN training stage was to obtain the relationship between feature sets and classification categories. The second step was to use a more flexible classifier, PNN, which was employed to discriminate between cover images and the stego images. Finally, according to the classification results, the detection accuracy was calculated. The security of the proposed method against second-order SPAM features is presented in Table 7. From the SPAM detection results shown in Table 7, we can see that the accuracy, precision, recall, and F1 score were 53.54%, 52.4%, 77.6%, and 62.6%, respectively. Table 7 shows that the SPAM features cannot effectively identify the stego images generated using the proposed method and the cover images. This verifies that the stenography method proposed in this study is effective and robust against second-order SPAM features.
5 Conclusion
The evaluation of information hiding technologies involves comparison of the steganographic capacity and digital image quality. The steganography method proposed in this study can effectively improve steganographic capacity and digital image quality. A PSNR of above 50 dB or an SSIM value of 0.999 still indicates a very high image quality. As those values are achieved even with the maximum possible embedding capacity, this verifies that the stenography method proposed in this study is effective. The steganography method was applied after excluding the overflow blocks. According to the different steganographic images, scanning was conducted in rows or columns, and the differences were recorded. The proposed steganography method was applied to the images with a higher sum of those whose differences were 1 and − 1, through which the steganographic capacity was improved by 3.8–20.29%. The average steganographic capacity increment was approximately 9.15%. Furthermore, compared to PVO and PVOMM, the steganographic capacity was improved by nearly 1.78% and 0.51% while the PSNR value was reduced only by approximately 1.5 and 0.6, respectively, indicating that the differences of rows or columns dynamically selected in this study can effectively improve the steganographic capacity.
Abbreviations
- EC:
-
Embedded capacity
- HS:
-
Histogram shifting
- IPVO:
-
Improved PVO
- LM:
-
Location map
- LSB:
-
Least-significant bit
- MSE:
-
Mean square error
- PE:
-
Prediction error
- PEHS:
-
Prediction error histogram shifting
- PNN:
-
Probabilistic neural network
- PSNR:
-
Peak signal-to-noise ratio
- PVD:
-
Pixel-value differencing
- PVO:
-
Pixel value ordering
- PVOMM:
-
PVO multi-pixel modification
References
F.-A.-P. Petitcolas, R.-J. Anderson, M.-G. Kuhn, Information hiding—a survey. Proc. IEEE 87(7), 1062 (1999)
C.-K. Chan, M. Cheng, Hiding data in images by simple LSB substitution. Pattern Recogn. 37, 469–474 (2004)
D.-C. Wu, W.-H. Tsai, A steganographic method for images by pixel-value differencing. Pattern Recogn. 24, 1613–1626 (2003)
H.-C. Wu, N.-I. Wu, C.-S. Tsai, M.-S. Hwang, Image steganographic scheme based on pixel-value differencing and LSB replacement methods. IEEE Proc. Vision Image Signal Process. 152(5), 611–615 (2005)
Z. Ni, N. Y-Q Shi, W.S. Ansari, Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 16(3), 354–362 (2006)
J.-H. Hwang, J.-W. Kim, J.-U. Choi, A reversible watermarking based on histogram shifting. Lect. Notes Comput. Sci 4283, 348–361 (2006)
M. Fallahpour, M.-H. Sedaaghi, High capacity lossless data hiding based on histogram modification. IEICE Electron. Expr. 4(7), 205–210 (2007)
H.-W. Tseng, C.-P. Hsieh, Reversible data hiding based on image histogram modification. Imaging Sci. J. 56(5), 271–278 (2008)
X. Zhang, Reversible data hiding in encrypted image. IEEE Signal Proc. Let. 18(4), 255–258 (2011)
C. Qin, C. Chang, Y. Chiu, A novel joint data-hiding and compression scheme based on SMVQ and image inpainting. IEEE Trans. Image Process. 23(3), 969–978 (2014)
S. H Huang, Y.L. Li, in 2012 Eighth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Piraeus. Multi-level reversible data hiding with pyramidal structure (2012), pp. 234–237
W. Hong, T.-S. Chen, C.-W. Shiu, Reversible data hiding for high quality images using modification of prediction errors. J. Syst. Softw. 82(11), 1833–1842 (2009)
P. Tsai, Y.-C. Hu, H.-L. Yeh, Reversible image hiding scheme using predictive coding and histogram shifting. Signal Process. 89(6), 1129–1143 (2009)
K.-S. Kim, M.-J. Lee, H.-Y. Lee, H.-K. Lee, Reversible data hiding exploiting spatial correlation between sub-sampled images. Pattern Recogn. 42(11), 3083–3096 (2009)
X. Li, J. Li, B. Li, B. Yang, High fidelity reversible data hiding scheme and prediction-error expansion. Signal Process. 93(1), 198–205 (2013)
F. Peng, X. Li, B. Yang, Improved PVO-based reversible data hiding. Digital Signal Process. 25, 255–265 (2014)
X. Qu, H.-J. Kim, Pixel-based pixel value ordering predictor for high-fidelity reversible data hiding. Signal Process. 111, 249–260 (2015)
X. Wang, J. Ding, Q. Pei, A novel reversible image data hiding scheme based on pixel value ordering and dynamic pixel block partition. Inf. Sci. 310, 16–35 (2015)
Y.-T. Chen, C.-S. Tsai, H.-C. Wu, in Master’s thesis, National Chung Hsing University, R.O.C. A study on high capacity reversible information hiding using pixel-value-ordering and multi-pixel modification (2016)
A. Westfeld, A. Pfitzmann, in Proceedings of the 3rd International Workshop on Information Hiding. Attacks on steganographic systems (1999), pp. 61–75
J. Fridrich, M. Goljan, D. R, Detecting LSB steganography in color and gray-scale images. IEEE Multimedia 8(4), 22–28 (2001)
X. Zhang, S. Wang, Vulnerability of pixel-value differencing steganography to histogram analysis and modification for enhanced security. Pattern Recogn. Lett. 25(3), 331–339 (2004)
W.-C. Kuo, Y.-H. Lin, Y.-Z. Huang, Y.-C. Lee, in Proceedings of the 7th Conference on Information Technology and Applications in Outlying Islands. On the security of histogram-based reversible data hiding (2008), pp. 205–208
C.-L. Liu, H.-H. Liu, Reliable detection of histogram shift-based steganography using payload invariant features. Appl. Mech. Mater. 284, 3517–3521 (2012)
C.-F. Lee, C.-C. Chang, J.-J. Li, Y.-H. Wu, in 2016 Nicograph International. A survey of reversible data hiding schemes based on pixel value ordering (2016), pp. 68–74
Bows-2 image database. http://agents.fel.cvut.cz/boss/index.php?mode=VIEW&tmpl=credits. Accessed on 10 May 2015
A.-M. Eskicioglu, P.-S. Fisher, Image quality measures and their performance. IEEE Trans. Commun. 43(12), 2959–2965 (1995)
Z. Wang, A.-C. Bovik, H.-R. Sheikh, E.-P. Simoncelli, Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process. 13(4), 600–612 (2004)
Structural similarity. https://en.wikipedia.org/wiki/Structural_similarity. Accessed on 20 Nov 2018
T. Pevný, P. Bas, J. Fridrich, Steganalysis by subtractive pixel adjacency matrix. IEEE Trans. Inf. Forensic Secur. 5(2), 215–224 (2010)
Acknowledgements
This study was supported by the Ministry of Science and Technology of the Republic of China under Grant MOST 106-2221-E-606-002.
Funding
The initial stage of this research was funded by the Ministry of Science and Technology of the Republic of China under Grant MOST 106-2221-E-606-002, for the August 2017–July 2018 duration.
Availability of data and materials
The cover images and stego images used in the experiment, the code of the proposed PVO steganography and related experimental data in this study can be disclosed. Please contact author for data requests.
Author information
Authors and Affiliations
Contributions
H-HL is the first author and the corresponding author. C-ML did some parts of the experiment. Both authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
This study is for academic research and submission purposes only. The authors in this study declare that they have no competing interests.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Liu, HH., Lee, CM. High-capacity reversible image steganography based on pixel value ordering. J Image Video Proc. 2019, 54 (2019). https://doi.org/10.1186/s13640-019-0458-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13640-019-0458-z